
While Tor makes it significantly harder to trace online activities, it does not guarantee complete anonymity. Internet service providers may also be suspicious of Tor usage and might monitor traffic patterns, even if they cannot see the content of the encrypted communications. Therefore, while Tor provides a strong layer of privacy, it is not an absolute shield against surveillance, and users should remain aware of this possibility. While it is true that the dark web is sometimes used for illicit purposes, not everything on the dark web is illegal. It also serves valuable goals, helping individuals communicate in environments hostile to free speech.
Connect To The Tor Network
- Research what they offer and assess your privacy needs to make a decision about which dark web browser works best for you.
- The safest and best dark web browsing tool for Android users is the official Tor Browser APK from the Tor Project site.
- It’s from this process of ‘peeling’ off the individual layers of encryption, like the layers of an onion, where ‘the onion router’ gets its name.
- Its RAM servers and Private DNS go a step further to protect your identity online.
- It will encrypt your traffic and data so no one can intercept it.
A VPN is a confusing factor for many because there are two ways to use it with Tor. It might be because of the poorly maintained site or Tor’s slow speed because of the way it works. Either way, some sites take up to a minute or more to load, so don’t fret. If you’re prompted to connect, click the purple “Connect” button and wait for a few seconds. We already know of one necessary component needed for this – Tor. However, while Tor is great, safe, and whatever you think, it’s not as great as another component – a VPN.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
Many mainstream media organizations monitor whistleblower sites looking for news. Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account. Tor has an in-build slider which lets you adjust the level of security. This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed.
Access The Dark Web Safely
- Some countries lack comprehensive cybercrime laws, complicating international efforts to combat dark web activities.
- It also adds a crucial layer of encryption before your traffic even enters the Tor network.
- Cryptocurrencies like Bitcoin are often used for illegal transactions due to their perceived anonymity, prompting legal scrutiny.
- This initiative aims to harmonize laws across countries, facilitating prosecutions and international cooperation.
- It includes media and archives which cannot be crawled and indexed with current search engine technology.
Unlike traditional websites, .onion addresses aren’t indexed by mainstream search engines, requiring specialized methods to find them safely and reliably. The most common tool for accessing the Dark Web is Tor (The Onion Router). Tor provides anonymity through a process known as “onion routing,” where internet traffic is encrypted and passed through multiple network nodes. Each node decrypts just enough data to know the next destination but not the origin, making tracing the connection back to the user exceptionally difficult.
What Is The Dark Web? Myths, Realities And Cybersecurity Risks
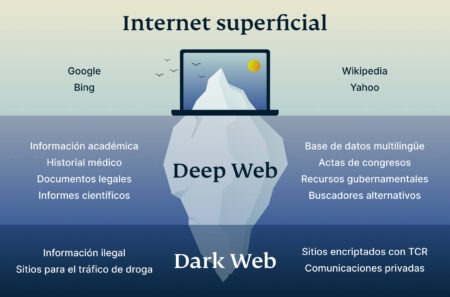
Content and services on the deep web are accessible through a regular browser. Search engines on the Dark Web function differently from those on the surface web. They are designed to index and retrieve information from hidden services that are not accessible through traditional search engines like Google or Bing.
The Impact Of AI On Cybersecurity Jobs Automation, Threats, And Fut

This browser encrypts your internet traffic and routes it through a network of volunteer-operated servers, making it difficult for anyone to trace your online activities back to you. It is also essential to be cautious when interacting with others on the Dark Web, as not everyone may have good intentions. Avoid sharing personal information and be wary of any requests for sensitive data or financial transactions.

Great life advice, but it’s even more valuable where the darknet is concerned. Keep in mind that many criminal organizations use the dark web to communicate or sell merchandise. You may very well end up in the middle of a stakeout that could turn ugly. So, if the website looks fishy, close the tab, and forget about it. We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those.
A Guide To Tor Web Browser: Is It Safe?

But if you’re serious about maximum privacy, it’s absolutely worth the effort. It’s ideal for journalists, activists, or anyone who needs to browse without leaving digital footprints. And yes, it also works perfectly for those who just want to explore the dark web with peace of mind.
How To Get Started With Tor Browser – A Web Browser Designed For Privacy
Granted, criminals do gravitate towards darknet sites in order to perform unlawful activities. But does that mean that simply accessing the dark web is illegal? If you ever land on a questionable site, it’s smart to check whether your data is secure.
This means that while dark web search engines are useful, you still need extra privacy tools to make sure your browsing can’t be linked back to you. The Tor Project provides versions of the Tor Browser tailored for various operating systems, ensuring compatibility across different devices. Once the download is complete, the user needs to locate the file and double-click it to initiate the installation wizard.
Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably. This means the Tor Browser is not recommended for streaming video, playing games, or downloading large files. In an onion network, messages are encased in layers of encryption, much like the layers of an onion. The encrypted data is sent through a series of network-based nodes called onion routers. Another great source to find and explore dark web marketplaces or other sections is to visit Reddit’s resourceful forum.
What Is The Dark Web? Here’s How To Access It Safely (and What You’ll Find)
Agencies like the FBI and Europol have developed specialized cybercrime units with advanced tools to address these challenges. These units often conduct undercover operations to gather intelligence and evidence. The takedown of AlphaBay, a major dark web marketplace, was achieved through international cooperation, demonstrating the importance of cross-border collaboration. Cryptocurrencies like Bitcoin are often used for illegal transactions due to their perceived anonymity, prompting legal scrutiny. Governments have implemented measures to trace and regulate cryptocurrency transactions. In this guide, we’ll cover the dark web access guide, explain how to use Tor browser safely, and answer key questions like is it safe to browse the dark web.



