
Tor users in the USA, in particular, may want to use a VPN, which will be faster and more reliable. Our rigorous research and testing have revealed revealing truths and busted myths. We’ll navigate this intricate maze with you, uncovering its secrets while ensuring your online safety.
It allows access to the .onion sites on the dark web that you won’t find using a regular browser. To bolster foundational cybersecurity measures, security teams need to incorporate dark web insights into broader threat intelligence programs. These insights provide context around cyber risks and help security teams adjust their defenses. “By having insights into the dark web, security professionals have a better understanding of threat actor behaviors and motivations,” Currie says. This is in part a response to exit scams, such as what AlphV/BlackCat and other marketplaces have pulled.
Conclusion: Safeguard Your Brand Against Dark Web Threats
- Silk Road, operational from 2011 until its shutdown by the FBI in 2013, demonstrated the scale of these marketplaces, with thousands of users worldwide.
- Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc.
- That means setting up encrypted email with a new email address, encrypting messages with PGP, using a pseudonym, setting up an anonymous Bitcoin wallet, disabling Javascript in Tor Browser, researching vendors, and more.
- Market listings on these platforms often carry the same professional touch you’d expect from legitimate sites complete with product descriptions, seller ratings, and even customer reviews.
Continuous monitoring of stealer logs, credential leaks, and dark web chatter should be a core function of threat intelligence, not an occasional sweep after an incident. “It’s a live reconnaissance zone,” says Ensar Seker, CISO at SOCRadar. Threat actors target organizations based on exposed credentials, stale access points, or misconfigured assets advertised or sold. A lot of this information is inexpensive and readily available — opening the door to attacks. It offers outstanding privacy features and is currently available at a discounted rate. Identifying specific individuals who use the dark web can be quite tricky.

The Increasing Risk Of Data Breaches
There are different levels of security in the browser that are worth considering. To review security settings, click on the onion logo in the top left and select “Security Settings”, which will bring up a slider offering a choice of the default of standard, or safer and safest. In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play. Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites. When you use the Tor network, your traffic is layered in encryption and routed via a random relay, where it’s wrapped in another layer of encryption.
Shuttered Dark Web Marketplaces
- One of the key factors driving the growth of these markets is the diversity of products available.
- Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa.
- In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web.
- The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
Because Tor nodes are made up of volunteers, not all of them play by the rules. The final relay before your traffic goes to the destination website is known as the exit node. The exit node decrypts your traffic and thus can steal your personal information or inject malicious code. Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either. So, if you want to know how to access the dark web safely, you need to understand that the vast majority of the dark web, or dark net, is only accessible through the Tor browser. It’s like an iceberg – The visible tip above water, known as the “surface web” represents the familiar, searchable content.
The stolen data included names, contact information, and order histories. Dark web listings surfaced almost immediately after the breach, advertising this information for sale to cybercriminals. An award-winning cybercrime threat intelligence firm, KELA’s mission is to provide 100% real, actionable intelligence on threats emerging from the cybercrime underground, to support the prevention of digital crimes. This article reveals the top 10 dark web markets dominating in 2025, their unique characteristics, and the critical implications for enterprise cybersecurity. When one goes down, two more emerge with new ideas, better technology, and greater difficulty to track.
Additionally, multi-signature transactions are increasingly common, requiring multiple parties to approve a payment, further enhancing trust between users. One of the key factors driving the success of darknet markets is the emphasis on vendor ratings and product diversity. Users can access detailed reviews and ratings for each vendor, ensuring that they engage only with trusted sellers. This system fosters a competitive environment where vendors strive to maintain high standards, resulting in better quality products and services. Additionally, the wide range of available products caters to diverse preferences, making these markets a one-stop solution for users. To minimize risks when exploring darknet markets, you need the right set of tools.
Browse Privately
These resources can be instrumental for businesses with limited budgets. Providing regular training on phishing prevention and cybersecurity best practices empowers employees to recognize and avoid potential threats. This means that the identities and locations of darknet users are hidden from public view and remain anonymous, even when interacting with other users or engaging in any online activity. As such, you should exercise caution when accessing any unofficial dark websites. There are many different ways to access the dark web, but navigating it can be tricky and dangerous if you don’t know what you’re doing. A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web.
Dark Web Statistics For 2025: Key Trends And Threats
Staying safe on the dark web requires even more vigilance than the public internet. Scammers and criminals are lurking everywhere to take advantage of the unwary. Follow the pointers below to avoid becoming a victim if accessing the dark web. In addition to these tools, you need to exercise extreme caution when browsing on the dark web because there are tons of phishing and malicious sites on there. Only use .onion links that come from legitimate sources like The Hidden Wiki.
The Internet’s Biggest-Ever Black Market Just Shut Down Amid A Telegram Purge
The breach also exposed operational vulnerabilities, as the company’s incident response plan proved inadequate to contain the attack. Data breaches also present a critical challenge, as stolen credentials allow attackers to infiltrate systems and extract sensitive information, including customer data and trade secrets. These breaches can result in regulatory penalties for failing to comply with frameworks such as GDPR or HIPAA. For example, non-compliance can result in fines of up to 4% of an organization’s global annual revenue. Many dark websites are perfectly legal and safe to use and, in many cases, are better for your privacy than clear websites. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing.
The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. When you search for something on Google or Bing, you’re using the clear web. Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands. Get Avast BreachGuard for PC to protect your privacy and keep your personal data from falling into the wrong hands. Avast BreachGuard monitors the dark web for data breaches around the clock.
However, they aren’t visible on the open internet and require specialized browsers like Tor to access. This added layer of encryption masks users’ locations, making it nearly impossible to trace activity back to individuals. Data breaches like the ones mentioned above highlight the significant threats posed by dark web black markets. Stolen data can quickly transition from legitimate systems to underground forums, where it becomes a valuable commodity for cybercriminals. To counter these risks, organizations need robust, proactive solutions that go beyond traditional cybersecurity measures. This is where Brandefense’s Dark Web Monitoring Solution plays a critical role.
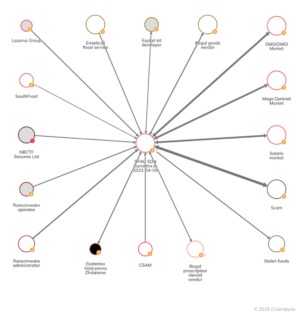
When accessing the dark web, the first step is to install a dark web-friendly browser on your computer. Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address. The success of OMs is also contingent on the level of participation and use of OMs’ functions. In addition to institution-based trust, online purchase intentions are influenced by the perceived social presence of a marketplace and the perceived social presence of others (Lu et al., 2016).
“But much of this appears to be driven around a need for criminal threat actors to get convenient access to quick payments from victims in order to support further operations,” he adds. Increasingly, privacy-focused coins such as Monero (XMR) and Zcash (ZEC) are being adopted to protect anonymity and make tracing funds difficult for law enforcement. Between 2023 and 2024, the share of new darknet marketplaces accepting only Monero rose from just over one-third to nearly half, reflecting a clear trend toward anti-surveillance tactics, according to Kurrie. It’s fragmenting into specialized communities that include credential marketplaces, exploit exchanges for zero-days, malware kits, and access to compromised systems, and forums for fraud tools. “Some migrate to private forums, other ransomware groups, create new ransomware groups, or adopt decentralized technologies like blockchain-based hosting or intermittent access platforms that are harder to trace and takedown.

This adds extra protection since opening Tor itself encrypts your traffic. The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there. As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across. ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. Well, now it’s time to fire up Tails and do a little bit of tinkering.



