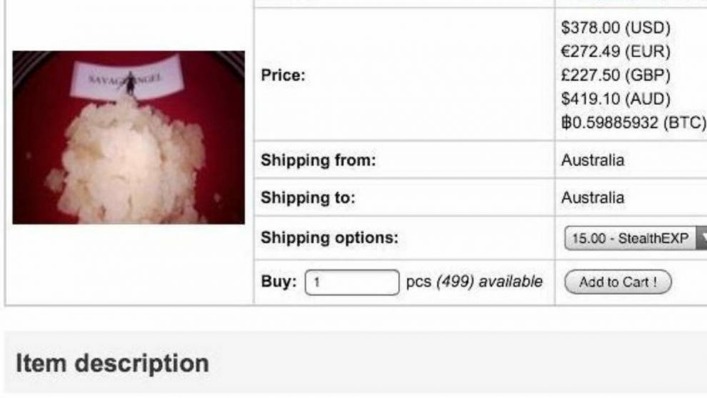
Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. The dark web is also a place for scammers to attract vulnerable and unwitting victims. The platform is also used by governmental cyber departments to identify and track potential criminals or offenders.
Top VPN Deals
Organizations also have a responsibility to safeguard the personal information of their customers or users. This requires implementing robust data protection measures, educating employees about cybersecurity best practices, and following regulatory guidelines and compliance standards. Law enforcement agencies and cybersecurity firms actively work to combat the trade of personal information on the dark web. They employ advanced techniques to track down cybercriminals, dismantle illegal networks, and raise awareness about the importance of data security. To protect against the threats posed by malware and botnets, individuals and organizations should adopt a multi-layered approach to cybersecurity. This includes utilizing robust antivirus software, regularly updating operating systems and applications, implementing strong firewalls, and educating users about basic cybersecurity practices.

Bonus: The Silk Road
A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically. Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data. BidenCash shop was established in April 2022, following the seizure of other card shops and carding platforms by the Russian authorities. Since its inception, it has been attracting the attention of both old and new cybercriminal customers.
- Stricter regulations, international cooperation, and increasing awareness about ethical organ donation can help eradicate this illegal trade and ensure safe and legitimate organ transplantation practices.
- With the rise of technology and the internet, a whole new realm of online marketplaces has emerged, including the infamous Dark Web.
- It has gained notoriety for being a hub for illicit activities, such as selling drugs, weapons, stolen data, and other illegal goods and services.
- For example, the deep web is often a platform used by political activists who own a blog.
- Through collaboration with international partners, these agencies aim to dismantle trafficking networks and prosecute those responsible for this heinous crime.
White House Market
For all of the money spent by police in these investigations, it’s fair to say that the net result from a user’s perspective is simply the inconvenience of a few searches, followed by registration at a new service. The dark web model endures because it offers great efficiencies to dealers and users. Since the demise of Wall Street and Dream, two new markets, Empire and Nightmare – which both opened over a year ago – have grown rapidly as users have migrated over from closed sites. Today, Empire has over 28,000 drug listings and Nightmare has over 60,000.

What Makes A Dark Web Market Different From Regular Online Stores?
While it hosts legitimate uses, such as protecting privacy in oppressive regimes, it is also infamous for facilitating illegal trade in drugs, weapons, counterfeit documents, and stolen corporate data. To buy his fentanyl, the man uses “darknet” sites, which are unlisted on search engines, rely on a special private browser for access, and don’t tie his username to his identity. He says most of the sites on the regular internet, which the Senate report focused on, are scams in which dealers will take money and fail to deliver. (The Senate investigators did not actually make any purchases.) Or, these so-called “clearnet” sites lead to arrests. Remember, accessing and participating in Dark Web marketplaces is illegal and rife with risks.
Tweak Tor Browser Settings
The dark web provides an avenue for counterfeiters to sell fake currencies, including banknotes from various countries. These counterfeit bills are often sold at a fraction of their face value, attracting buyers looking to profit from the illegal circulation of money. By being vigilant and taking necessary precautions, individuals and organizations can help protect themselves and minimize the impact of stolen data on the dark web. It is important to remain informed about emerging threats and actively participate in efforts to enhance cybersecurity. The sale of stolen data on the dark web poses a significant threat to individuals and organizations alike.
Step 2: Obtain Required Tools

Like other marketplaces, ASAP Market also requires you to register for an account. DarkOde Reborn is a great darknet market where you can find anything you want. The website has a great design and a clean and organized interface that is easy to use. The homepage includes options like browsing products, searching, mixer, and coin exchange.
- Also called the Dark Web, the Deep Web is huge part of the internet that standard search engines can’t find, like the giant mass under the tip of an iceberg.
- To get on the dark web, you need a browser built for the job, and the best in the business is Tor.
- This adds an extra layer of protection to thwart tracking and monitoring in case the traffic passes through a compromised exit node.
- Exploring the realm of credit card transactions on the Dark Web is a journey into a dangerous and illegal world.
- Last month, the city of Providence, Rhode Island approved the establishment of what will be the state’s first safe injection site, and the only one to operate outside of NYC thus far.
- You can either sell or buy goods on the dark web, but both present difficulties.
It undermines legitimate healthcare systems, compromises patient safety, and hinders efforts to combat the abuse and misuse of prescription drugs. Organizations have a responsibility to implement robust security measures to protect user account information. This includes enforcing password requirements, implementing multi-factor authentication, encrypting sensitive data, and educating users about best practices in account security. Data breaches, hacking incidents, and phishing scams are some of the ways cybercriminals obtain personal information. The dark web serves as a marketplace for selling and purchasing this stolen data, allowing criminals to profit from the exploitation of innocent individuals.
There’s no escrow system when you do that and, therefore, no guarantee they’ll actually send you something. Being able to order drugs for self-medication so easily and discreetly, Marie continued, also kept misguided friends from trying to force her to quit. Contrary to popular belief, making a loved one become abstinent (even if you can) won’t cure the underlying issues that may have led them to use in the first place. For people who use opioids, it also increases their risk of overdose when they resume use with lower tolerance.
Terence decided to begin buying online because—as a mid-career professional and father from Minnesota, now in his late 30s—he no longer has the connections that he did when he was formerly addicted to heroin. He wanted to be able to buy high-quality psychedelics from a trusted, reliable source and the dark web seemed like the best place to do so. Coauthor Dr. Monica Barratt, a senior research fellow at RMIT University in Melbourne, Australia, said that this potential mismatch between expectation and reality is what motivated the team to conduct the research. Did you know you can verify any unconfirmed Bitcoin transaction with our Bitcoin Block Explorer tool? Create an account with a username, password, and email and complete the captcha.
With the rise of technology and the internet, a whole new realm of online marketplaces has emerged, including the infamous Dark Web. The Dark Web is a hidden part of the internet that is not indexed by search engines and can only be accessed through specific software or networks. It has gained notoriety for being a hub for illicit activities, such as selling drugs, weapons, stolen data, and other illegal goods and services. These illegal activities are made possible by the layer of anonymity provided by Tor and other similar networks. Examples include the sale of high-quality products with low risk for contamination (including lacing and cutting), vendor-tested products, sharing of trip reports, and online discussion of harm reduction practices. By remaining vigilant, promptly reporting fraudulent activity, and implementing robust security measures, individuals and businesses can contribute to reducing the trade of stolen credit card details on the dark web.
The dark web serves as a breeding ground for the sale and distribution of malware and botnets, posing significant threats to individuals, businesses, and the overall cybersecurity landscape. Malware refers to malicious software designed to gain unauthorized access, disrupt operations, steal sensitive information, or launch cyber-attacks. Botnets, on the other hand, are networks of infected computers that are hijacked and controlled by cybercriminals. Firstly, using counterfeit money is illegal and can result in criminal charges if caught. Additionally, individuals who unknowingly accept counterfeit bills can suffer financial losses and damage to their reputation if the counterfeit is later detected. No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action.
Failing to monitor these underground forums can expose companies to financial losses, reputational damage, and compliance violations. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. New and potentially more vulnerable population segments can be reached by exploitative drug dealers as they begin to sell on social platforms and the number of drug consumers in the US and around the world grows. Lastly, remember that the traditional web offers countless legitimate ways to engage in online transactions and protect personal information. Explore trusted websites and platforms that prioritize cybersecurity, privacy, and legal compliance. Wizardshop.cc was established in 2022, and offers a wide range of leaked CVVs, database dumps and even RDPs.

The Evolution Of Dark Web Marketplaces
The availability of dangerous weapons in the hands of individuals who may not have undergone proper training or background checks increases the likelihood of criminal activity, including acts of terrorism and violence. Also typically sold in bulk, bank account and routing numbers surface every day on the dark web. In the examples below, the criminal is selling US business banking information, stating that the information is perfect for committing ACH transfer fraud.



