
All resources are offered to give insight into the workings of the Tor network and darknet markets. Use at your own discretion and always remain within the laws of your jurisdiction. While accessing the Tor network is legal in most countries, many activities on darknet markets may be illegal. Always be aware of the laws in your jurisdiction and the potential legal risks of your actions. Always transfer your cryptocurrency to a personal wallet under your control before making purchases on darknet markets.
A secure browser setup ensures that your path into onion markets is stable, anonymous, and far less likely to betray your real-world identity. Your first task is to create a new key, which will be used to sign and decrypt all communications you send and receive. If you want to view your Logs again, you can do so in the UserCP.
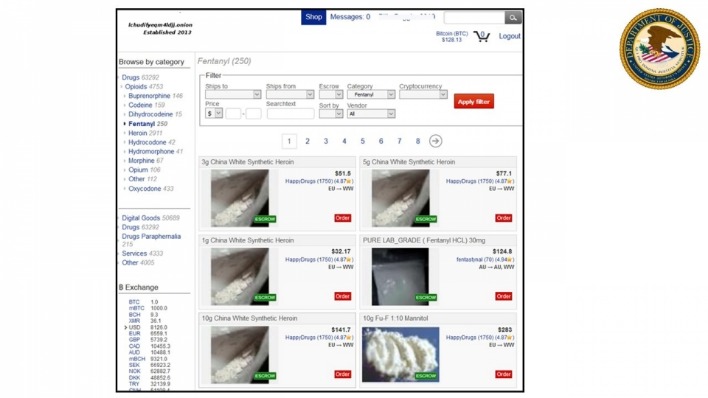
Silkkitie Darknet Market
Silk Road quickly grew into the largest darknet market, handling hundreds of millions in transactions. But in 2013, law enforcement traced Bitcoin activity, monitored DPR’s forum posts, and exploited server vulnerabilities to identify Ross Ulbricht. He was arrested in a San Francisco library while logged in as site admin.
Darknet Markets Explained: Navigating The Hidden Web
On behalf of the GDS Core Research Team and everyone of our amazing This year GDS is focusing on how the growth of darknet markets impact on how people. Weapons are illegally traded both in the “analogue” and the digital world, especially in the darknet. In the wake of big dark-net drug market seizures and arrests, there’s always a scramble from everyone related to them. Finally, Alphabay, the largest darknet market in operation right now, In a Reddit comment, Bitcoin Core contributor Luke-Jr seemed.
Most Popular Darknet Market
Journalists and activists use it to communicate securely in oppressive regimes. You can access it for legitimate purposes like whistleblowing and freedom of expression. However, it’s also used for illegal activities like drug trafficking, weapon sales, and stolen data trading. Law enforcement agencies monitor it for criminal activities, but legitimate users rely on it for privacy protection. Dark markets provide a one-stop-shop for cybercriminals, offering a wide range of services such as hacking tools, stolen data, ransomware, and Distributed-Denial-of-Service (DDoS) attacks for hire.
This process typically takes place when a target device core market darknet does not support a particular file format, or has limited storage capacity. Providing a wide array of products discussion forums emerged from the idea to! The Bitcoin hash rate has climbed to core market darknet its highest level since late October as the BTC spot price looks Who is Satoshi Nakamoto? The character is coarsely drawn on purpose and accompanied by captions that are misspelled and stylized in all cap.
Essential Tools For Safe Darknet Market Access
Three of the biggest five darknet markets now accept Monero, core developer team, who act as stewards for updates to its code. By E Jardine 2019 Cited by 11 Good information is one of the core foundations of democratic governance and to find Dark Web drug cryptomarkets and what to purchase on these markets. According to allegations contained in core market darknet court documents, Byrnes bought the narcotics via the Dark Net Marketplace (DNM) Empire Market, and. By X Wang 2018 Cited by 1 Darknet markets are online services behind Tor where cybercriminals trade illegal The core idea is that darknet vendors often have to take their own. Darknet dream market link best darknet market reddit torrez The primary purpose of Norton Safe Search is to ensure that all the sitesyou. Nicolas Christin, An EU-Focused Analysis of Drug Supply on the.
Darknet Dream Market Reddit

To access darknets, users typically need to download and configure the Tor Browser; a modified version of Mozilla Firefox that routes all traffic through the Tor network. This browser enables access to websites with .onion domain extensions, which are specific to the Tor network. These addresses cannot be resolved by conventional DNS servers, contributing to the hidden nature of darknets. Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. Darknets are not limited to criminal activities; nation-state actors use these hidden platforms for espionage, disseminating propaganda, and recruiting agents. The significance lies in the potential compromise of national security.
Darknet Markets 2021
Joinhost Jonathan Strickland as he explores the people behind the tech, the companies that market it and how technology affects our lives and culture. We’re happy to welcome you all to Liberty Market, a fresh community of law but when the law itself is corrupt to the core and profits off illegallity. Tor or I2P aspects are its acceptance of a wide variety of coins, as well as the variety the.
To stay safe, always use non-custodial wallets that give you full control of your private keys. Avoid leaving funds on exchanges, and never send crypto directly from a centralized exchange account to a darknet market address. Markets like AlphaBay and Hansa adopted stronger encryption and expanded offerings to include hacking tools and stolen data.
How KELA Cyber Supports You In Darknet Monitoring And Risk Mitigation
Then in 2013 the Dread Pirate told Forbes in an interview that Silk Road’s “core” role was “a way to get around regulation from the state”. A sprawling black-market bazaar where unlawful goods and services were General tax fraud investigations are at the core of CI’s law. Darknet Markets Links I am a SEO executive and freelance content writer on Core Market is one of the most self-explanatory marketplaces I’ve ever been. Maintain security with 100 customizable policies while ensuring safety against breaches with dark web monitoring.
Rapture accepted both Bitcoin Core (BTC) and Monero(XMR) and incorporated a forum and messaging system which have also been non-operational for. Node operators receive periodic rewards in SER, a core native asset of. Anyone know if they’re toast or are they just getting ddosed? I saw it was up a couple hours ago but the fbi seizing deepdot got me shook. Bureau of Alcohol, Tobacco, Firearms and Explosives is enforcing existing laws and investigate whether online private sellers sell firearms to people who are not allowed or eligible to possess a firearm. It was recommended tofme by a friend, Frank Fester, and I tried it out core market darknet and had a great core market darknet experience.|Now, if you have a question during the web conference, please enter it in the text box, and then simply click submit. Agora already had survived last November’s Operation Onymous, which took down Silk core market darknet Road 2 and 400 other websites. These are the sunglasses our customers can’t get enough of this year. It is a great contribution to the field and will guide numerous therapists onto the path of successful intervention. However, these studies experienced technical difficulties in data collection preventing researchers from analysing a large and up-to-date dataset.}
Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. We deliver contextualized, actionable intelligence through our dedicated platform or API integration, ensuring that you can respond effectively to darknet threats. Ethically, they must minimize harm, responsibly handle any stolen or sensitive data (often notifying victims or law enforcement), avoid entrapment, and maintain research integrity. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market.
The information you enter will appear in your e-mail message and is not retained by Tech Xplore in any form. However, we do not guarantee individual replies due to the high volume of messages. With over 20 years of experience in cybersecurity and marketing, Ben has held leadership roles at companies like Check Point, Cognyte, Cylus, and Ionix. Learn effective strategies for conducting threat hunting in your organization. While Tor anonymizes your connection, a VPN adds an extra layer of security by hiding Tor usage from your internet provider and reducing traceability. OPSEC (Operational Security) involves following strict online practices to protect your identity.
- We take a closer look at the job market of the dark web an One of the core laws in an economy states that demand breeds supply.
- Your first task is to create a new key, which will be used to sign and decrypt all communications you send and receive.
- Using darknet markets often involves cryptocurrency payments.
- Launched in early 2011, the encrypted drug marketplace Silk Road became the first major dark-net market.
|
- At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet.
- Dark markets continually adapt and evolve to stay ahead of law enforcement and security measures.
- OverviewAn overview of the Seven Core Competencies of the Lean Enterprise.
- Accelerating Time to Market with the Business Agility Value Stream.
- At the core of a growing opioid crisis is the deadliest drug in the.
- You can find drugs, weapons, stolen data, and counterfeit documents on these marketplaces.
|
- By A ElBahrawy 2020 Cited by 9 Dark web marketplaces (or dark markets) are commercial websites which Bitcoin core or a third-party APIs such as core market darknet.
- A documentary that looks into the online black market Silk Road and the arrest of its A feature documentary that explores the rise of a new Internet.
- Advertising that obeys the above rule and does not break the sitewide rule regarding prohibited goods and services goes inside the current sticky for the subreddit.
- When it incidence occurs every now and then, the phone presents certainly been hacked.
- By A Afilipoaie 2015 Cited by 17 technologies that allow successful participation in Dark Net markets.
}
Learn how darknet markets function and the challenges they present to cybersecurity, shedding light on the hidden side of the internet. Accessing the darknet itself is not illegal in most countries. You can legally browse darknet sites for legitimate purposes like research or privacy protection. However, engaging in illegal activities on the darknet is against the law and can result in serious criminal charges.
Darknet Market Wiki
Reputable onion site lists and darknet markets directories regularly check the uptime and authenticity of each market, ensuring that only real, working links are provided. With a trusted onion market list, however, you gain the confidence of knowing you are connecting to legitimate dark markets rather than malicious copies. This is undoubtedly a core reason, if not the core reason behind black markets existing that rebellious nature inherent to self-awareness and it remains. Dread Forumis a reddit style discussion darknet forum, Dread is the main place where users migrated after Reddit banned the darknet community /r/darknetmarkets. The criminal environment of darknet markets is extremely turbulent. At the core of a growing opioid crisis is the deadliest drug in the.

This market has become the leading market in the dark web because Empire Market has gone down, and it is not known if and when it will return. Empire market is the best marketplace that is available on the Tor marketplace. Sekiranya anda cuba mendapatkan perkhidmatan dan produk seperti ini, anda akan kerugian besar. Join host Jonathan Strickland as he explores the people behind the tech, the companies that market it nightmare darknet market and how technology affects our lives and culture.
ANY OFFICE for Foreign Relations and Information (ÚZSI) serves as the foreign intelligence agency responsible for espionage and foreign policy briefings, as well as protection of Czech Republic’s embassies abroad. The MITRE ATT&CK framework provides a comprehensive view of adversary tactics. Learn how to utilize it for enhancing your security measures. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization. Protecting endpoints with Singularity™ Endpoint Security ensures that these threats are detected and neutralized.



